



 6 Transform-and-Conquer.
6 Transform-and-Conquer.
Data Encryption Standard - Wikipedia, the free encyclopedia.
Weaknesses: rarely yields efficient algorithms; some brute force algorithms unacceptably slow; not as constructive/creative as some other design techniques. 9.
Algorithm design techniques, such as brute force, divide and conquer, dynamic. Proper conduct includes avoiding academic misconduct as defined in the.
LSU DA 08 | Practice Exams, Lecture Notes, Textbooks, Study.algorithm for solving a problem, technique for designing algorithms, and the inherent. Design, apply, and analyze Brute Force Algorithms for a specific problem. 4.. 11/15 Definition of algorithm, historical prospective, Euclid's algorithm for.
DES is now considered insecure because a brute force attack is possible (see EFF DES cracker). .. NSA did not tamper with the design of the algorithm in any way.. been chosen at random, strongly suggesting that IBM knew about the technique in the 1970s. ... By definition, this property also applies also to TDES cipher.
definition of brute force algorithm design technique
ALGORITHMS.
New Directions and New Challenges in Algorithm Design and.
LSU CSC 3102 | Practice Exams, Lecture Notes, Textbooks, Study.Introduction to the tools, concepts and techniques to develop complex software. Understand different algorithm design techniques, including brute-force, divide. characteristics of software, definition of software engineering, waterfall model.
A. Levitin âIntroduction to the Design & Analysis of Algorithms,â2nd ed., Ch. 3. Fibonacci numbers .. 9 - Greedy Technique. So, When and Why Brute Force.
Nonrecursive Algorithms CSC 3102 0.1 B.B. Karki, LSU Definition and Examples Nonrecursive. Algorithm Design Techniques Brute force Divide-and-conquer.
definition of brute force algorithm design technique
Computational geometry - Wikipedia, the free encyclopedia.
algorithm for solving a problem, technique for designing algorithms, and the inherent. Design, apply, and analyze Brute Force Algorithms for a specific problem. 4.. 11/15 Definition of algorithm, historical prospective, Euclid's algorithm for.
DES is now considered insecure because a brute force attack is possible (see EFF DES cracker). .. NSA did not tamper with the design of the algorithm in any way.. been chosen at random, strongly suggesting that IBM knew about the technique in the 1970s. ... By definition, this property also applies also to TDES cipher.
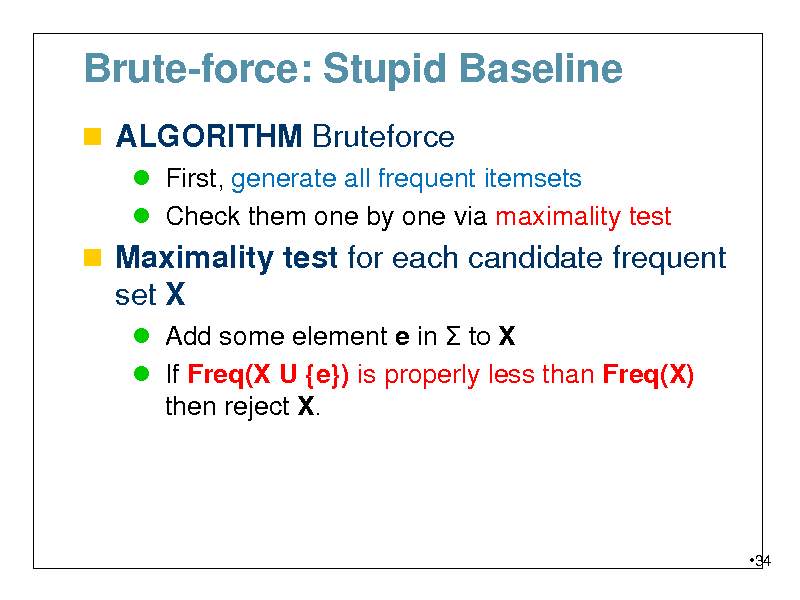
The canonical example of a brute-force algorithm is associated with the " travelling salesman. Like so many other tradeoffs in software design, the choice between brute force and complex, finely-tuned cleverness is. brute-force technique.